Idesco ID service
-
The platform is Azure cloud service (EU / Nordic countries)
-
Only Idesco can do this.
-
The validity time for a mobile ID is defined in your system.
-
Idesco ID does not store any data of the users. Only their phone number is needed, and for that, only temporarily, for registering the user. Their number is removable by command from your access control system, or configured for automatic removal.
-
- Reader/phone communications are secured behind strong AES encryption.
- All Idesco ID service transactions use the HTTPS protocol, with transaction destinations first authenticated only via a current, validated customer certificate.
-
Yes. Idesco ID does not interfere with daily access schedules or affect access rights. All mobile access control rights, groups and times are managed exclusively in your access control system, same as conventional access cards and tags.
-
8 byte / 64 bit, support for greater lengths is being developed for the future.
-
A mobile user’s UUID is created in your host system (most recommended). Our Idesco ID mobile application can also create one.
-
Idesco administers interface-specific data security certificates. These certificates also let us monitor
the number of credentials delivered to your users, which determines your invoicing.
Idesco ID app
-
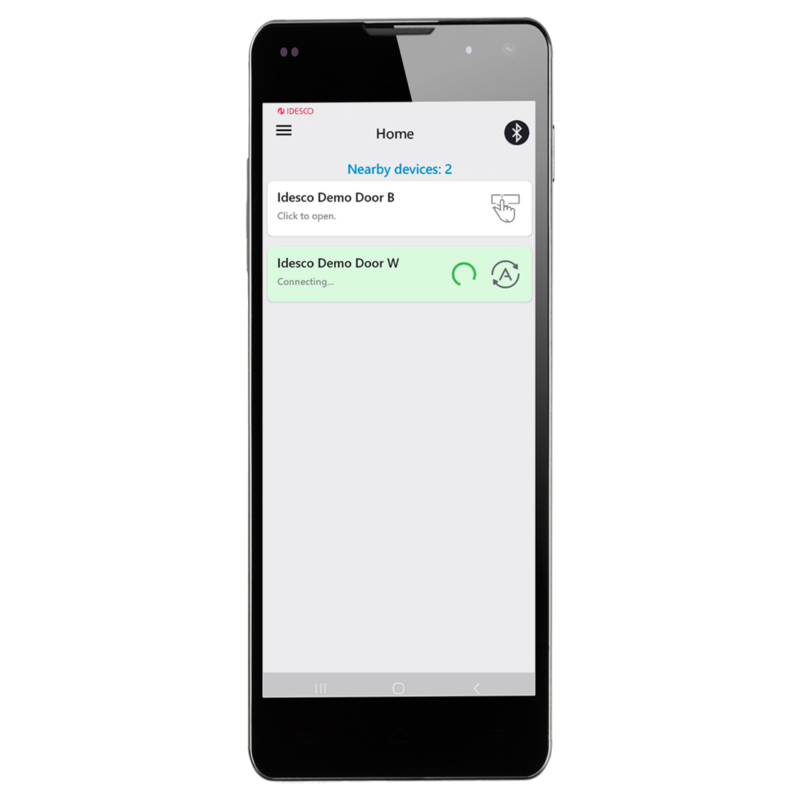
Yes, Idesco ID service and the Idesco ID mobile app support your phone possessing and using access privileges to numerous locations. A reader recognizes a user’s phone when they approach it. So, users won’t need to select the correct privilege from their phone before transacting the reader.
-
Only for downloading the application to the phone and then to register as a user.
-
Android / Apple
-
Idesco ID application supports three security levels for opening doors:
- Hands-free access, phone in the pocket
- Door is selected in the app by the user
- Door is opened only after phone’s own security unlock is entered
-
Idesco ID app is not yet compatible with NFC.
Mobile-enabled readers
-
Yes. For example, Idesco Mobile Coder app uses NFC.
-
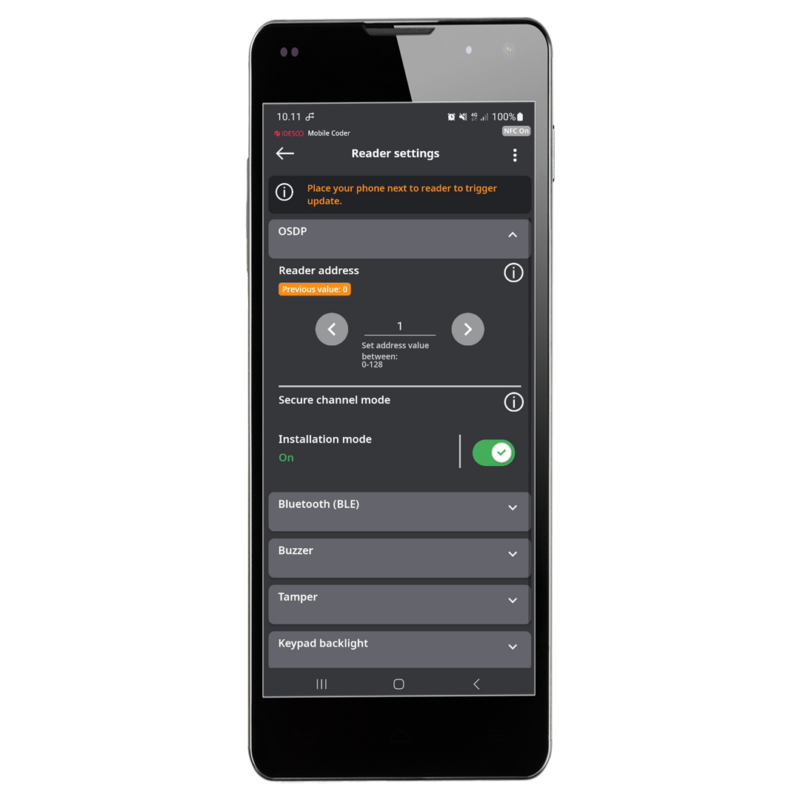
Idesco readers can authenticate a phone’s credentials via BLE at distances from a few centimeters out to 10 meters. Each reader’s preferred transaction distance can be assigned individually, and a badge-mode is also available. Lastly, transaction distance and other reader settings are quickly and easily programmed using our convenient Mobile Coder app.
-
Door names get stored in readers via Mobile Coder app. That application lets you assign the door name to a reader. When users approach the door, the Idesco ID app will display that door name to the user even if it is operating in the background.
-
-
Mobile credentials are always system-specific, which differentiates them.